Vida : Born after 2000, founder of Equation News, skilled in program trading. He has shared stories of making tens of millions of dollars in the crypto market.
Preliminary Context: At 01:23 AM Beijing Time on January 1, 2026, Equation News monitored: A market maker's Binance account was highly suspected to be compromised. The potential attacker was疑似 using approximately $10 million to $20 million from the account to集中 pump the price of the BROCCOLI714-USDT trading pair on the Binance spot market.
Below is the full text by Vida:
《Review: Making $1 Million in the Recent BROCCOLI714 Hack Incident》
Preconditions and Infrastructure:
- I had a long-term accumulated position of $200,000 in BROCCOLI714 at a cost of 0.016, purchased around early November this year. It included both spot and contract holdings. After buying, I was trapped and too afraid to even look at it.
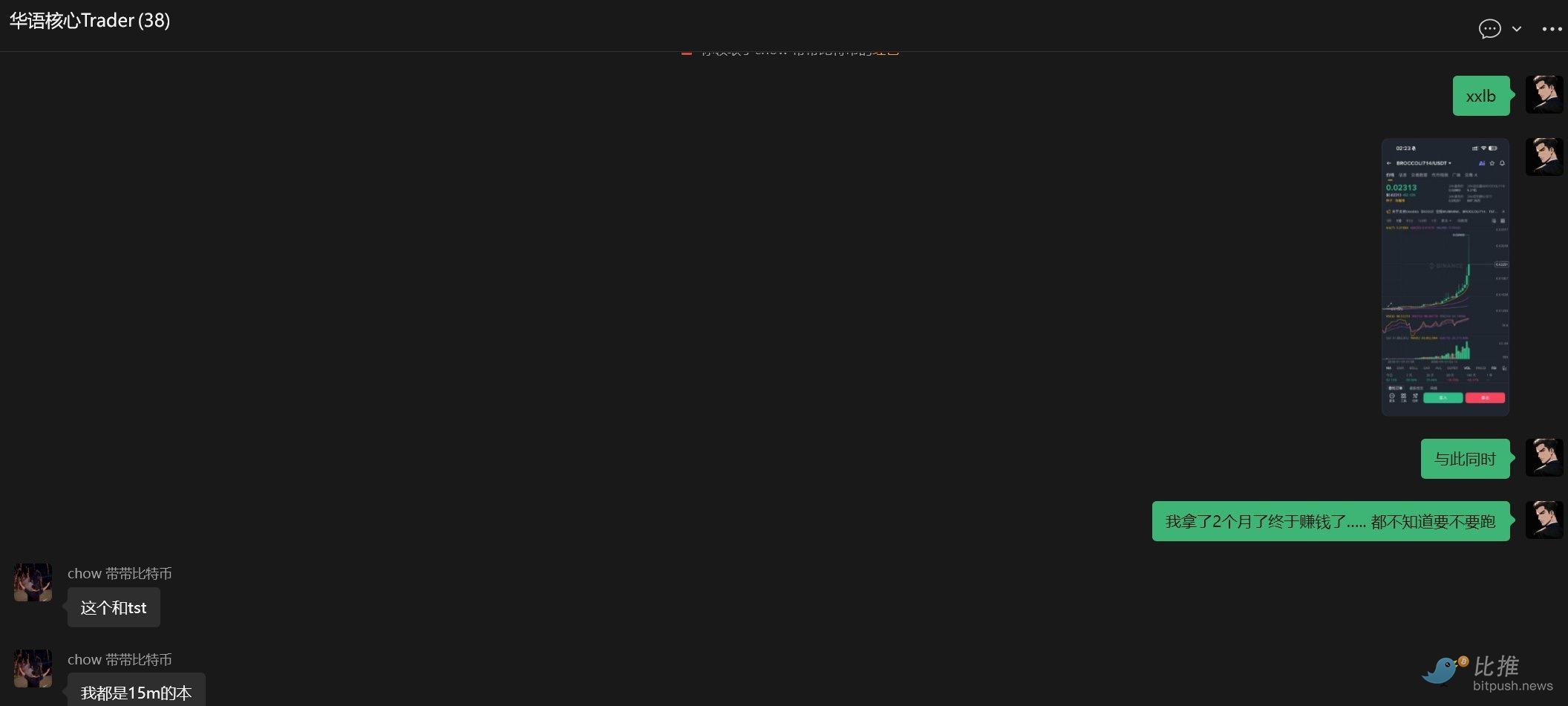
- The market maker's manipulation style in October-November was to rapidly pump the price within a few hours and then immediately dump with a large bearish candle. So, I set up an alert for my small-cap holdings that would wake me up if the price increased by over 30% within 1800 seconds.
- I also had a Binance perpetual contract funding rate arbitrage position for BROCCOLI714USDT with an average entry price of around 0.015 and a size of $500,000.
When the huge spot-contract price disparity occurred: My short-term surge alert program and my spot-contract spread alert program were both疯狂 alarming > prompting me to focus fully and rush to my computer to start working.
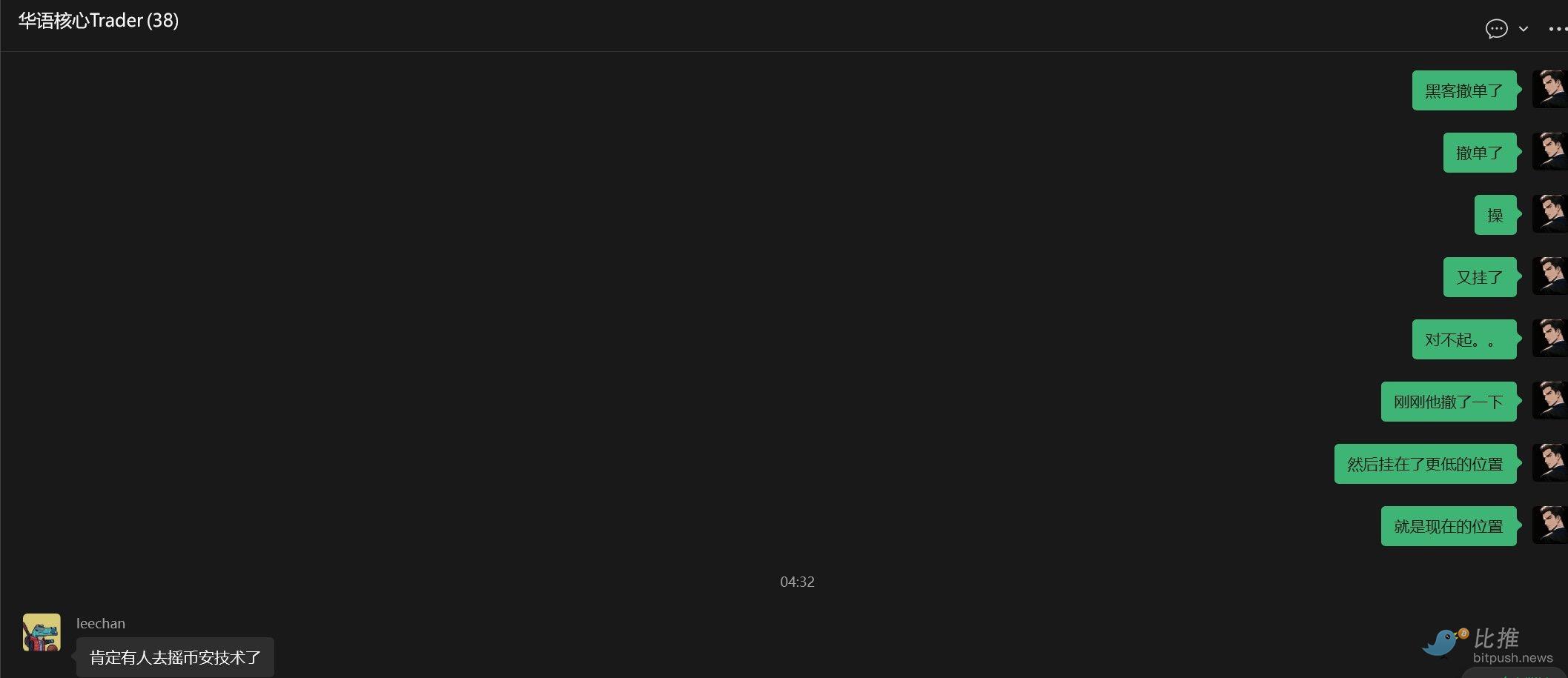
I第一时间 mentioned this situation in a core Chinese group on带带:
- My first reaction was to quickly close my funding rate arbitrage position. Because my original $500,000 arbitrage hedge position had become $800,000 in spot value and $500,000 in contracts. I immediately closed all arbitrage positions to lock in a profit of $300,000.
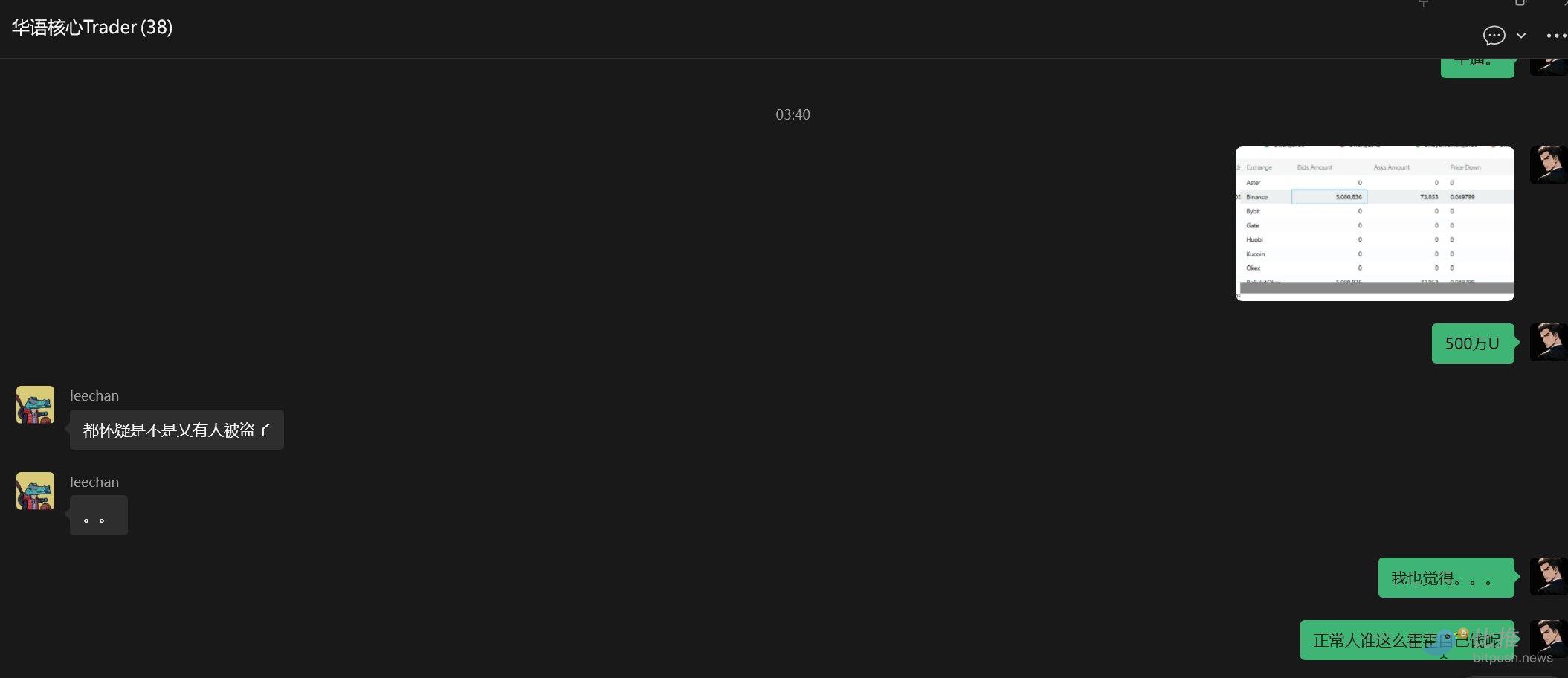
– But upon second thought, it felt very反常 because historically, no market maker would pump the spot market so violently regardless of the spread. I took a look at the order book depth and was震惊 to find that the bid-side 10% depth on Binance spot had $5 million in buy orders, while the contract side's bid 10% depth was only $50,000. Someone suggested a suspected Binance account hack, which I also found reasonable.
– I looked at the order book on the Binance main site again and was shocked to find that for BROCCOLI714, a coin with a market cap of $40m at the time, there were $26 million in bid orders. From this, I inferred that it must be either a hacked account or a market maker program bug, because no market maker would be foolish enough to play charity like this in the spot market.
So I monitored the changes in Binance's order book on one screen. I knew that as long as the hacker didn't withdraw the $20 million in buy orders on the spot market, the price of BROCCOLI714 would keep rising.
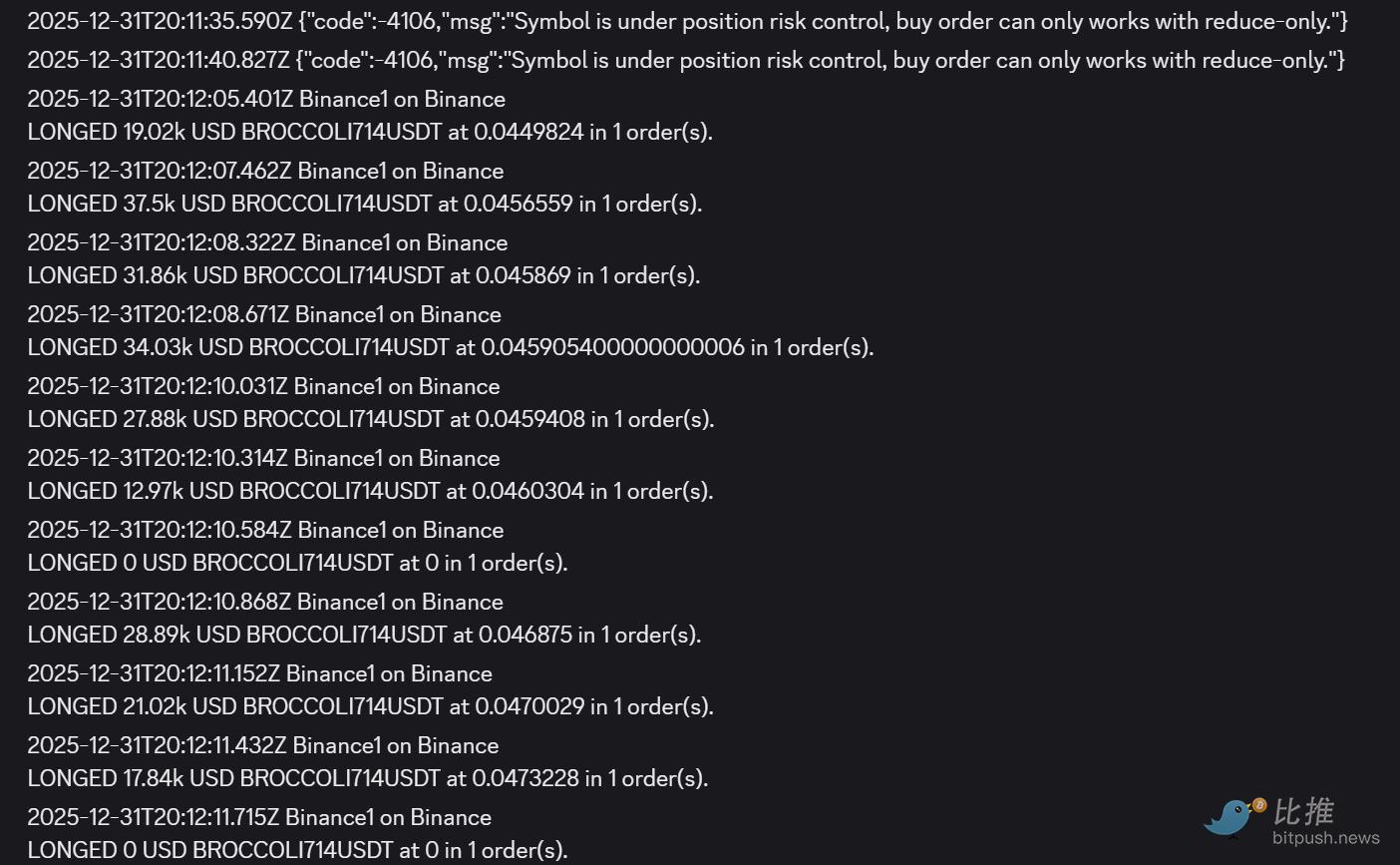
My first thought at this point was to go long on Binance contracts, but I found that the Binance contracts had already triggered the "circuit breaker protection mechanism" (reduce-only mode).
At that time, BROCCOLI spot was already at 0.07, while Binance contracts were capped at 0.038 by the circuit breaker mechanism, and Bybit contracts had risen to 0.055. So I chose to attempt a long position on the Binance BROCCOLI714USDT perpetual contract every 5-10 seconds on my trading terminal. If the order succeeded, it meant the circuit breaker period was over, meaning the Binance contract would pump.
I successfully蹲守到 this opportunity and added approximately $200,000 in long positions at a contract entry cost of 0.046.
So I kept watching the Binance spot order book.
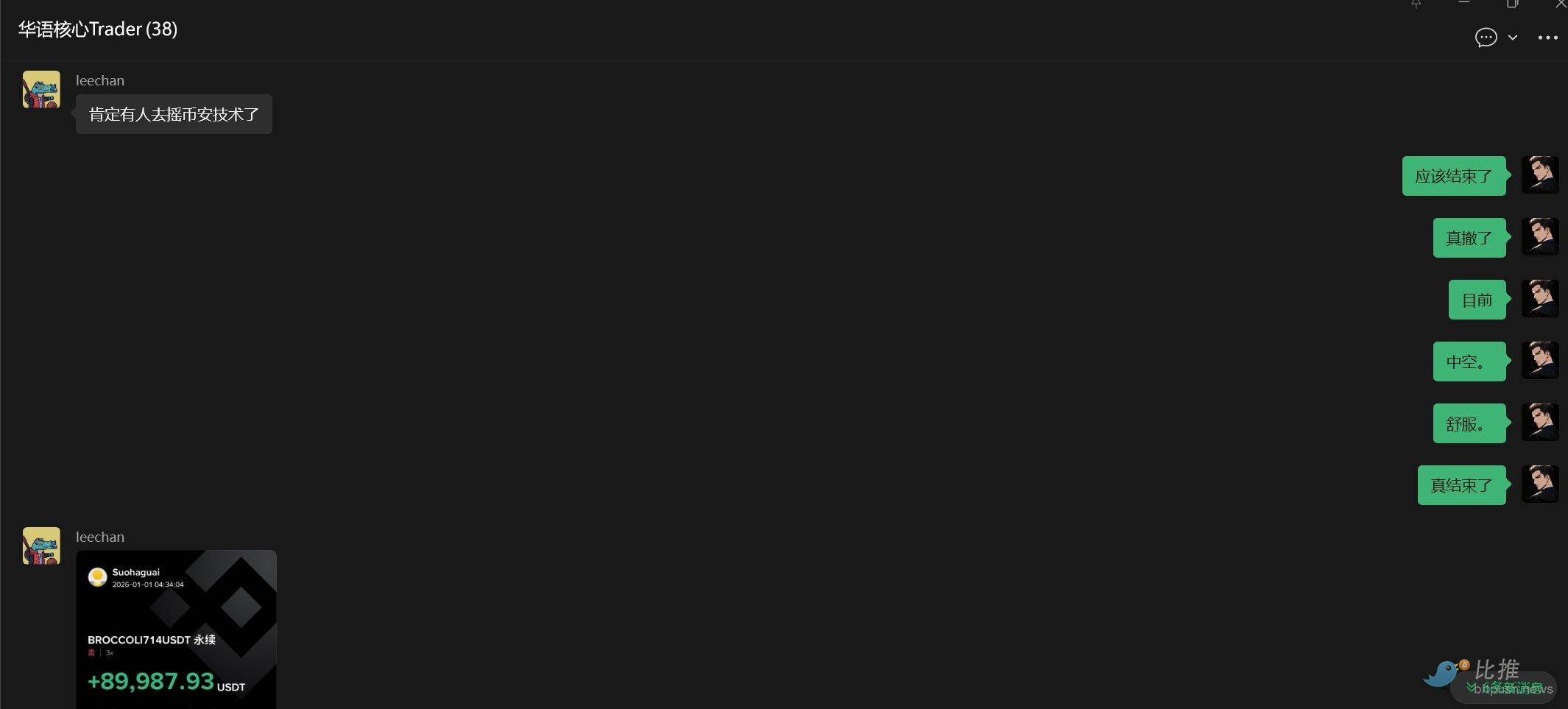
The hacker withdrew his orders once midway, leading me to believe he had been sanctioned by Binance's risk control department. So, at Beijing Time 2026-01-01 04:20:52.732, I started using my trading program to疯狂 sell > liquidate all my previously held + later added long BROCCOLI714 spot and contract positions regardless of cost.
My original $200,000 accumulated position + the later added $200,000 roughly cashed out to $1.5 million. (A lot of the original accumulated position was opened in the contract market, so I didn't capture as much premium)
After being scared off by the hacker's withdrawal of buy orders at 4:21, the不讲武德 hacker挂回 the buy orders about 1 minute later and directly pumped the price to 0.15.
But I knew he would eventually be sanctioned by Binance's risk control department. And once his account was risk-controlled > bids withdrawn > broccoli would crash, it was just that the staff might be lazy at 1.1 AM so he hadn't been risk-controlled yet.
So I kept a close eye on the order book.
Later, at 4:31, I noticed the hacker really withdrew all the bids. At 4:32, they were completely withdrawn. And this time, they didn't reappear for a long time + group friends said someone probably contacted Binance tech, and he was likely sanctioned.
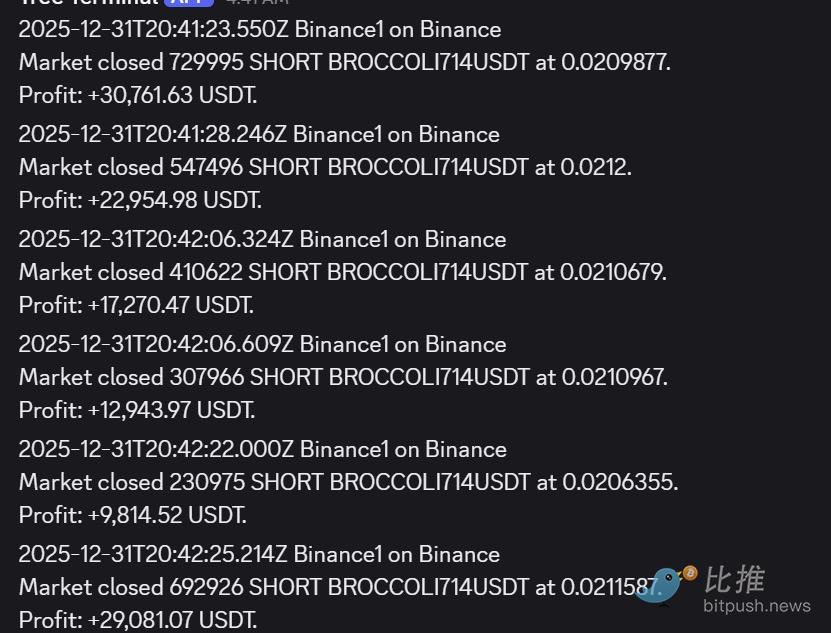
So I started shorting. I opened roughly $400,000 in short positions on Binance contracts at an average cost of around 0.065. The final closing price was approximately 0.02.
Revisiting why I was able to seize this opportunity:
1. Price anomaly alerts for small-cap strategies
- I set up short-term price surge alerts for small-cap strategies. As long as a held small-cap coin experiences an ultra-large price increase in a short time, it triggers a mandatory alert, 100% guaranteed to wake me up. – In the funding rate arbitrage strategy, I also set up monitoring: once a huge spread between spot and contract is detected, it triggers a mandatory alert.
2. Identifying反常 price action and verifying the order book
When I saw clearly反常 price action, the first thing I did was look at the order book to judge how much ammunition the "market maker" actually had. The result: For a coin with only a $30 million market cap, there were $20 million USDT in bids on the Binance spot side. From this, I judged this couldn't be normal market maker manipulation, but more like hacker behavior or a market maker's system bug (no market maker would pump the spot so recklessly and foolishly regardless of cost).
3. Still need to communicate more with experts. Brainstorming among several experts often helps figure out the entire剧本玩法 in the first moment.
4. I was very clear about the second phase玩法:
Wait for the hacker to be sanctioned by Binance's risk control department and withdraw the bid orders, then蹲守 this opportunity to short. So after completing the first phase of selling, I kept staring at the order book, waiting for this opportunity to appear. I waited over ten minutes and really managed to蹲守到 it.
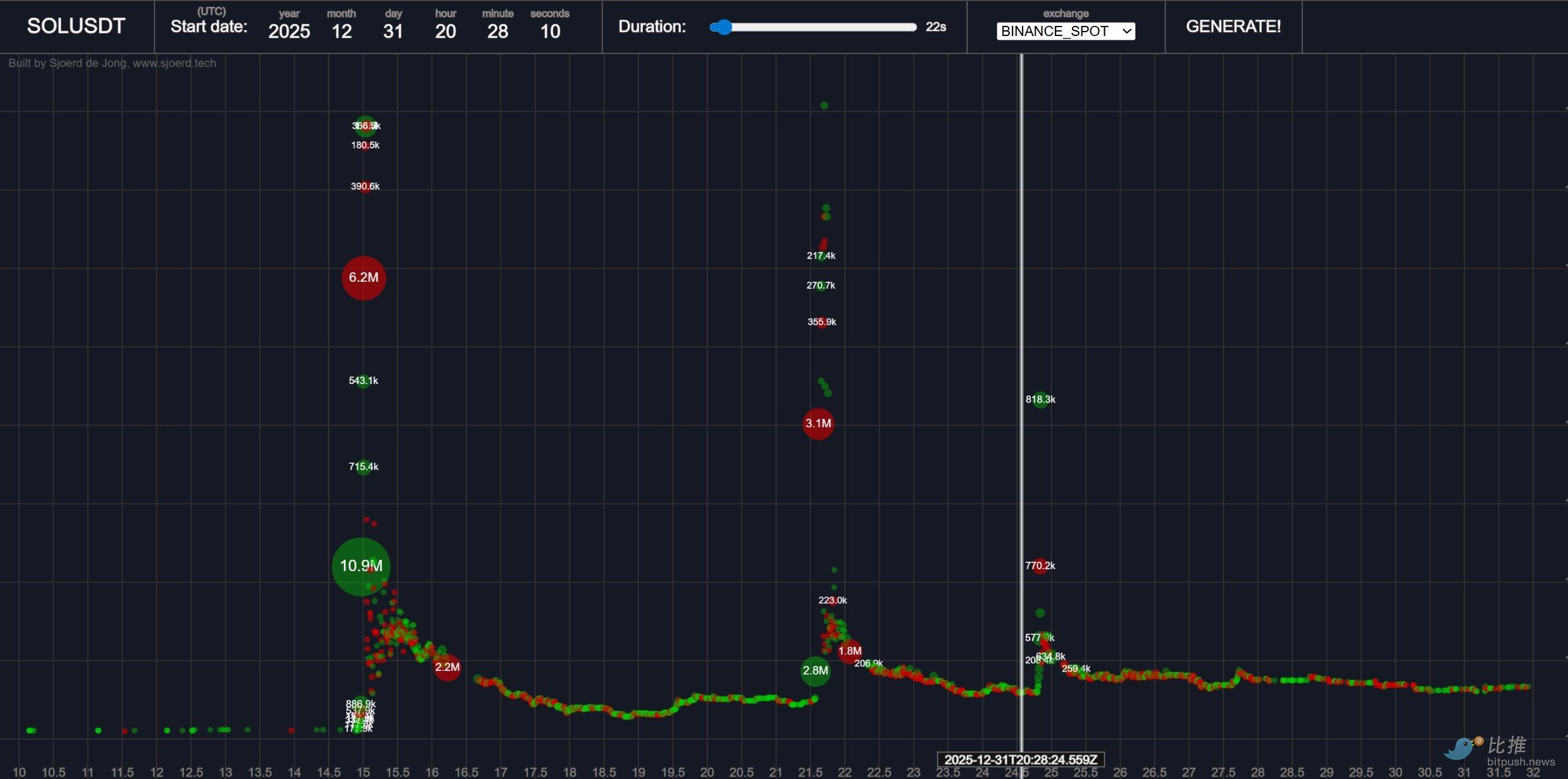
One behavior made me guess the BROCCOLI714 hacker was probably wrapping up, because at Beijing Time 4:28:15, he不计成本 bought SOLUSDT spot, pumping it by about 5% >>> which triggered my pre-set alert again, letting me know.
I guessed that his account might have been partially restricted by Binance from placing new orders in the BROCCOLI714 market, so he狗急跳墙 and bought SOL instead.
结果真的 (Sure enough), 3 minutes later the BROCCOLI price collapsed.
Twitter:https://twitter.com/BitpushNewsCN
Bitpush TG Discussion Group:https://t.me/BitPushCommunity
Bitpush TG Subscription: https://t.me/bitpush