As the Lunar New Year approaches, a time for bidding farewell to the old and welcoming the new, it is also a moment to reflect:
Over the past year, have you fallen into the trap of Rug Pull projects? Have you "bought at the peak" due to the hype from shilling KOLs? Or have you fallen victim to increasingly rampant phishing attacks, suffering losses from clicking malicious links or signing malicious contracts?
Objectively speaking, the Spring Festival does not create risks, but it can amplify them—when the frequency of fund movements increases, when attention is diverted by holiday arrangements, and when trading pace quickens, even the smallest mistake can easily escalate into a loss.
Therefore, if you are planning to adjust your positions or organize your funds around the holiday, it is advisable to conduct a "pre-holiday security check" on your wallet. This article will also systematically outline specific actions ordinary users can take, starting from several real and high-frequency risk scenarios.
I. Beware of "AI Deepfake" and Voice Simulation Scams
The recent viral SeeDance 2.0 has once again made everyone realize a fact: in the era of rapidly penetrating AGI, "seeing is believing, hearing is truth" is becoming obsolete.
It can be said that since 2025, AI-based video and voice fraud technologies have become significantly more sophisticated, including voice cloning, video face-swapping, real-time expression imitation, and tone simulation, all entering an "industrialized stage" of low门槛 and scalable replication.
In fact, with AI, it is now possible to accurately replicate a person's voice, speech rate, pauses, and even micro-expressions. This means that during the Spring Festival, such risks are particularly likely to be amplified.
For example, while you are on your way home or during a gathering with relatives and friends, a message pops up on your phone: a "friend" from your contact list sends a voice or video message via Telegram or WeChat, sounding urgent, claiming that their account is restricted, they need to transfer funds for red envelopes, or they need a small temporary advance in tokens, and requesting an immediate transfer.
The voice sounds natural, and the video even shows a "real person." With your attention diverted by holiday arrangements, how would you judge?
In previous years, video verification was almost the most reliable method, but today, even if the other party is talking to you via camera, it is no longer 100% trustworthy.
In this context, relying solely on a glance at a video or a snippet of audio is no longer sufficient for verification. A more prudent approach is to establish an independent verification mechanism with your core circle (family, partners, long-term collaborators) outside of online communication, such as offline code words known only to each other, or some detail questions that cannot be inferred from public information.
Additionally, it is necessary to re-examine a common path risk: links forwarded by acquaintances. After all, as per tradition, during the Spring Festival, terms like "on-chain red envelopes" and "airdrop benefits" are highly likely to become诱导 entries for viral spread in the Web3 community. Many people are not deceived by strangers but by trusting links forwarded by acquaintances, thus clicking on精心 disguised authorization pages.
Therefore, everyone must also remember a simple yet extremely important principle: do not click on any links of unknown origin directly through social platforms, and certainly do not authorize, even if they come from "acquaintances."
It is best to conduct all on-chain operations through official channels, bookmarked websites, or trusted entry points, rather than completing them in chat windows.
II. Conduct a "Year-End Cleanup" of Your Wallet
If the first type of risk comes from trust being forged by technology, then the second type of risk comes from the risk exposure we ourselves have accumulated over time.
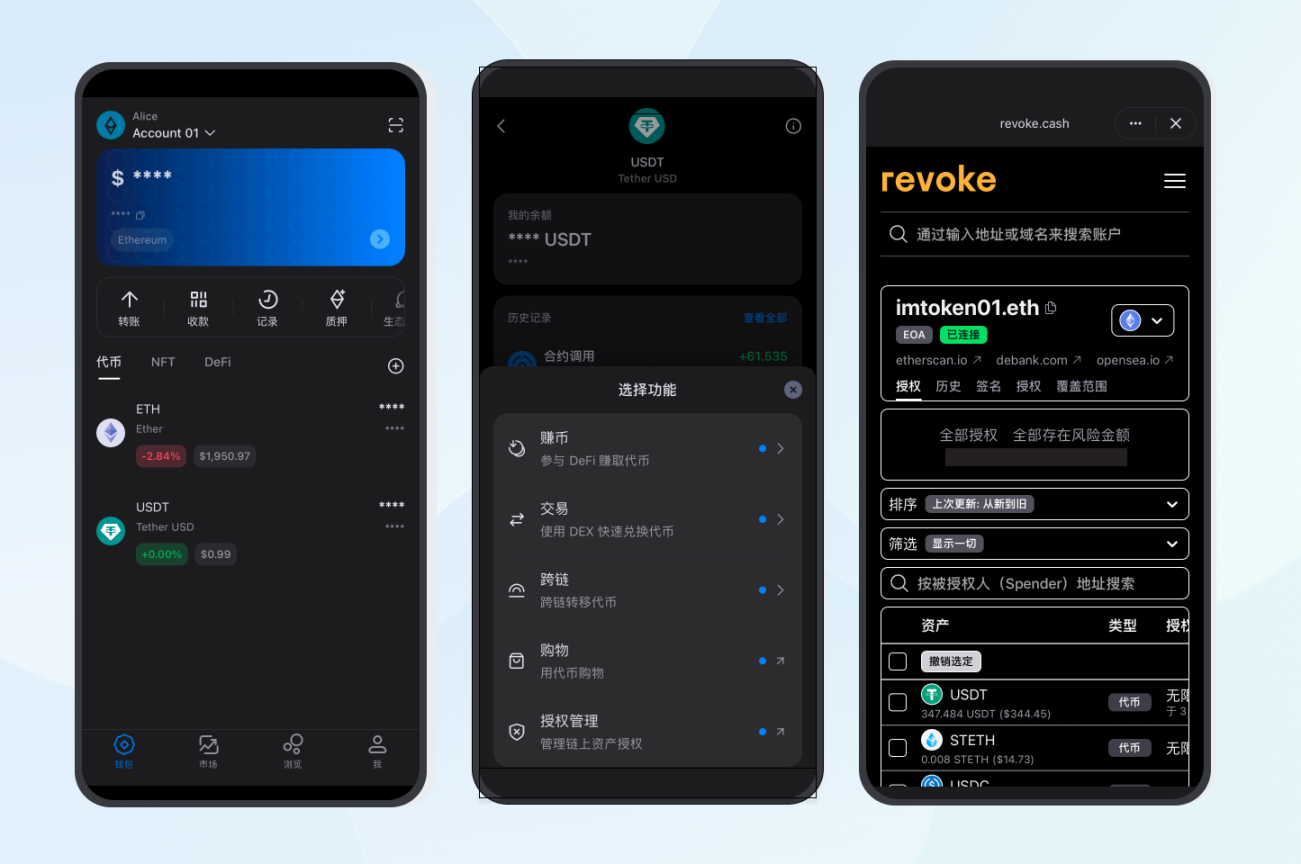
As is well known, authorization is the most basic yet easily overlooked mechanism in the DeFi world. When you operate in a DApp, you are essentially granting a token支配权 to a contract. This could be a one-time grant, an unlimited amount grant, short-term validity, or it could remain effective long after you have forgotten its existence.
Ultimately, it may not be an immediate risk point, but it is a持续存在的 risk exposure. Many users mistakenly believe that as long as assets are not stored in a contract, there is no security issue. However, during bull market cycles, users often frequently try various new protocols, participate in airdrops, staking, mining, and on-chain interactions, with authorization records continuously accumulating. When the hype subsides, many protocols are no longer used, but the permissions remain.
Over time, these excess historical authorizations are like a bunch of uncleaned keys. Once a protocol you long forgot has a contract vulnerability, it can easily lead to losses.
And the Spring Festival is a natural organizing node. It is a very worthwhile action to use the relatively calm pre-holiday time window to systematically check your authorization records:
Specifically, you can revoke authorizations that are no longer in use, especially unlimited authorizations; use limited authorizations for large assets held daily instead of长期开放全部余额 permissions; and separate long-term storage assets from daily operation assets, forming a structural分层 of hot wallets and cold wallets.
In the past, many users needed external tools (such as revoke.cash and other websites) to complete such checks. Nowadays, mainstream Web3 wallets like imToken have built-in authorization detection and revocation capabilities, allowing you to view and manage historical authorizations directly within the wallet.
In the final analysis, wallet security is not about never authorizing, but about the principle of least privilege—only granting necessary permissions for the present and收回 them promptly when they are no longer needed.
III. Do Not Slack Off in Travel, Social Interactions, and Daily Operations
If the first two types of risks come from technological upgrades and permission accumulation, respectively, then the third type of risk comes from environmental changes.
Spring Festival travel (returning home, traveling, visiting relatives and friends) often means frequent device switching, complex network environments, and密集 social scenarios. In such an environment, the脆弱性 of private key management and daily operations can be significantly amplified.
Seed phrase management is the most typical example. Saving screenshots of seed phrases in手机相册, cloud storage, or forwarding them to yourself via instant messaging tools is often done for convenience. However, in mobile scenarios, this convenience恰恰 constitutes the greatest hidden danger.
So remember, seed phrases must be physically isolated, avoiding any online storage methods. The bottom line of private key security is to stay offline.
Social scenarios also require boundary awareness. Displaying large asset pages or discussing specific holding scales during holiday gatherings is often unintentional but can lay the groundwork for future risks. Even more需要警惕的是, behavior that guides the download of disguised wallet applications or browser extensions under the guise of "exchanging experiences" or "teaching guidance."
All wallet downloads and updates should be completed through official channels, not through跳转 from social chat windows.
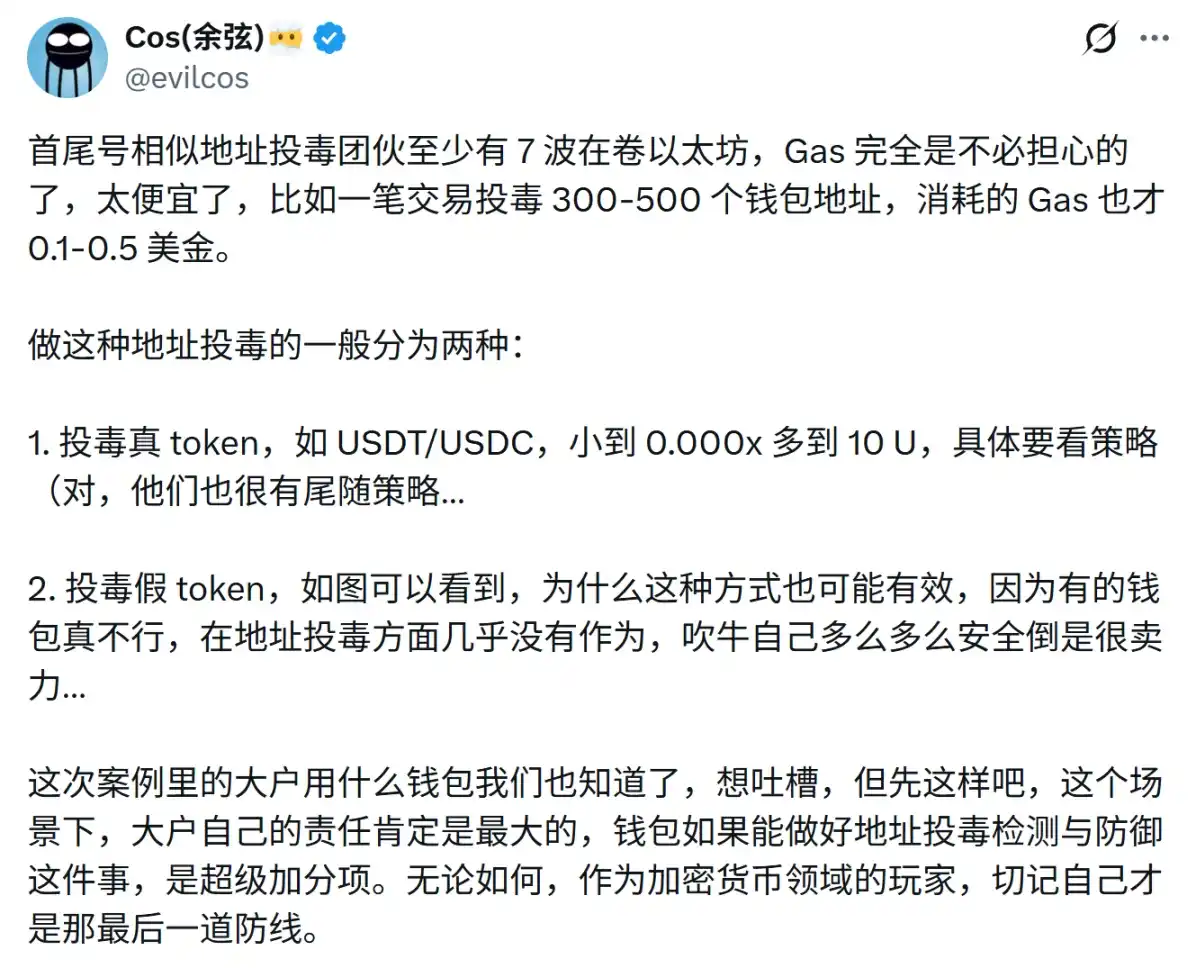
In addition, always confirm three things before transferring: network, address, and amount. After all, there have been too many cases of whales suffering significant asset losses due to误操作 from similar首尾号 address attacks, and such phishing attacks have become industrialized in the past six months:
Hackers often generate a large number of on-chain addresses with different首尾号 as a预备 seed library. Once a address receives a fund transfer from the outside, they immediately find an address with the same首尾号 in the seed library and then initiate an associated transfer through a contract, casting a wide net and waiting for a catch.
Since some users sometimes directly copy the target address from transaction records and only check the first and last few digits, they fall victim. According to Cos, founder of SlowMist, regarding首尾号 phishing attacks, "hackers are playing a撒网 attack, waiting for willing上钩, a game of probability."
Since the Gas cost is extremely low, attackers can batch poison hundreds or even thousands of addresses, waiting for a few users to make mistakes while copying and pasting. One success yields收益远高于成本.
These issues are not about how complex the technology is, but about everyone's daily operating habits:
- Check the full address characters, not just the beginning and end;
- Do not copy transfer addresses directly from history records without checking;
- When transferring to a new address for the first time, conduct a small test transfer first;
- Prioritize using the address whitelist function to manage frequently used addresses固定;
In the current decentralized system dominated by EOA accounts, users themselves are always their own first responsible person and last line of defense (extended reading "The $3.35 Billion 'Account Tax': When EOA Becomes a Systemic Cost, What Can AA Bring to Web3?").
In Conclusion
Many people always feel that the on-chain world is too dangerous and not user-friendly for ordinary users.
To be实事求是, Web3确实很难 provide a zero-risk world, but it can become an environment where risks are manageable.
For example, the Spring Festival is a time to slow down the pace and is also the most suitable time window of the year to organize risk structures. Instead of rushing to operate during the holiday, it is better to complete security checks in advance; instead of remedying afterwards, it is better to optimize permissions and habits提前.
Wishing everyone a safe and smooth Spring Festival, and may everyone's on-chain assets be stable and worry-free in the new year.