Author: Bitcoin Magazine Pro
Compiled by: Plain Language Blockchain
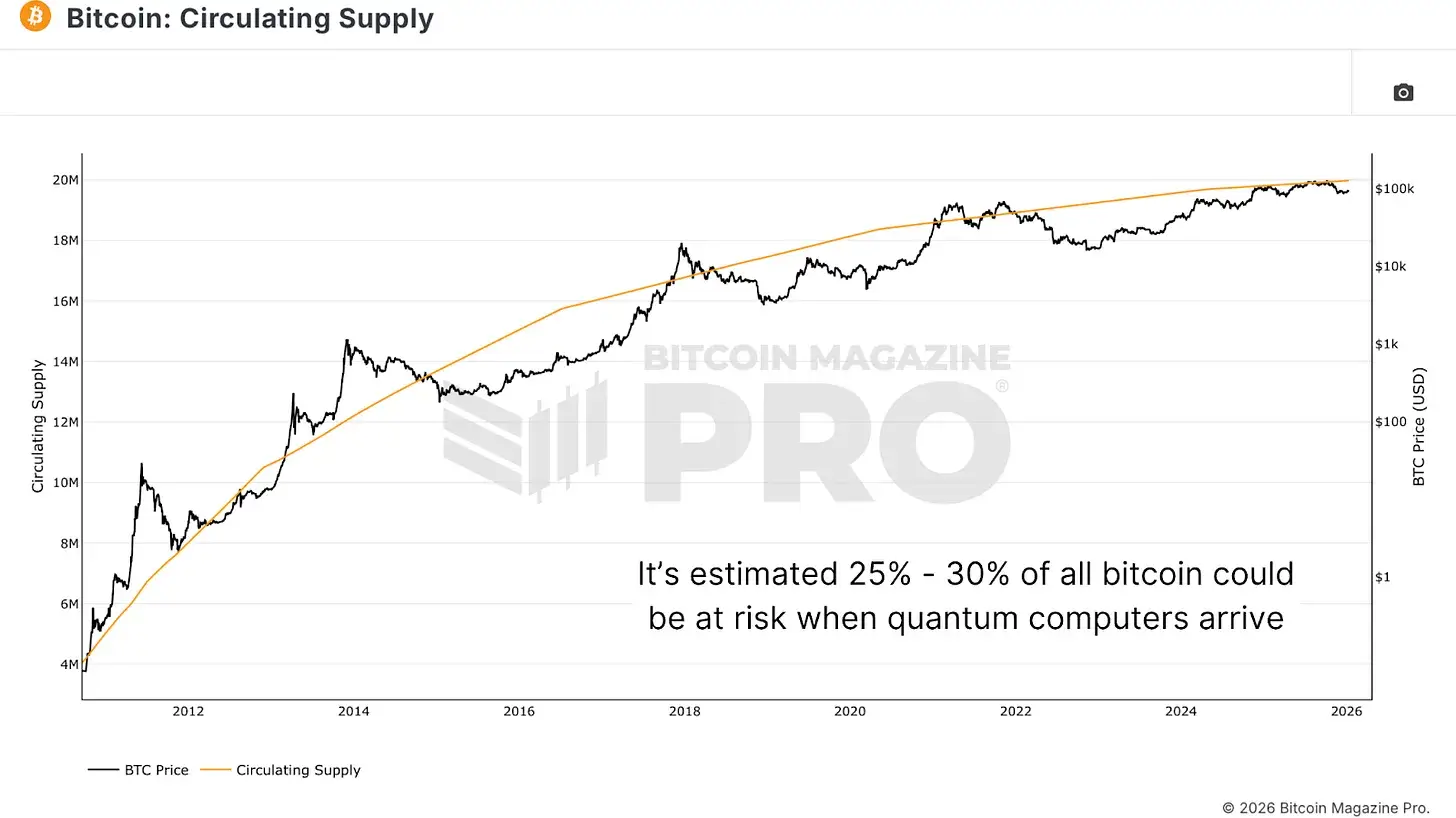
Bitcoin is facing its first real existential threat, not from government bans or market crashes, but from quantum computing. The 1.1 million bitcoins (worth approximately $100 billion) held in Satoshi Nakamoto's wallet, along with about 25% of the circulating supply, are currently exposed to outdated cryptographic keys that are highly vulnerable to quantum attacks. When quantum computers mature—whether in 5 or 25 years—these bitcoins will be cracked.
The Nature of the Threat
Bitcoin's security relies on the Elliptic Curve Digital Signature Algorithm (ECDSA). These algorithms make it extremely difficult to forge Bitcoin signatures mathematically without knowing the private key. For traditional computers, cracking such a signature would take millions of years. However, quantum computers operate entirely differently and have the potential to solve the discrete logarithm problem underlying ECDSA in minutes or hours.
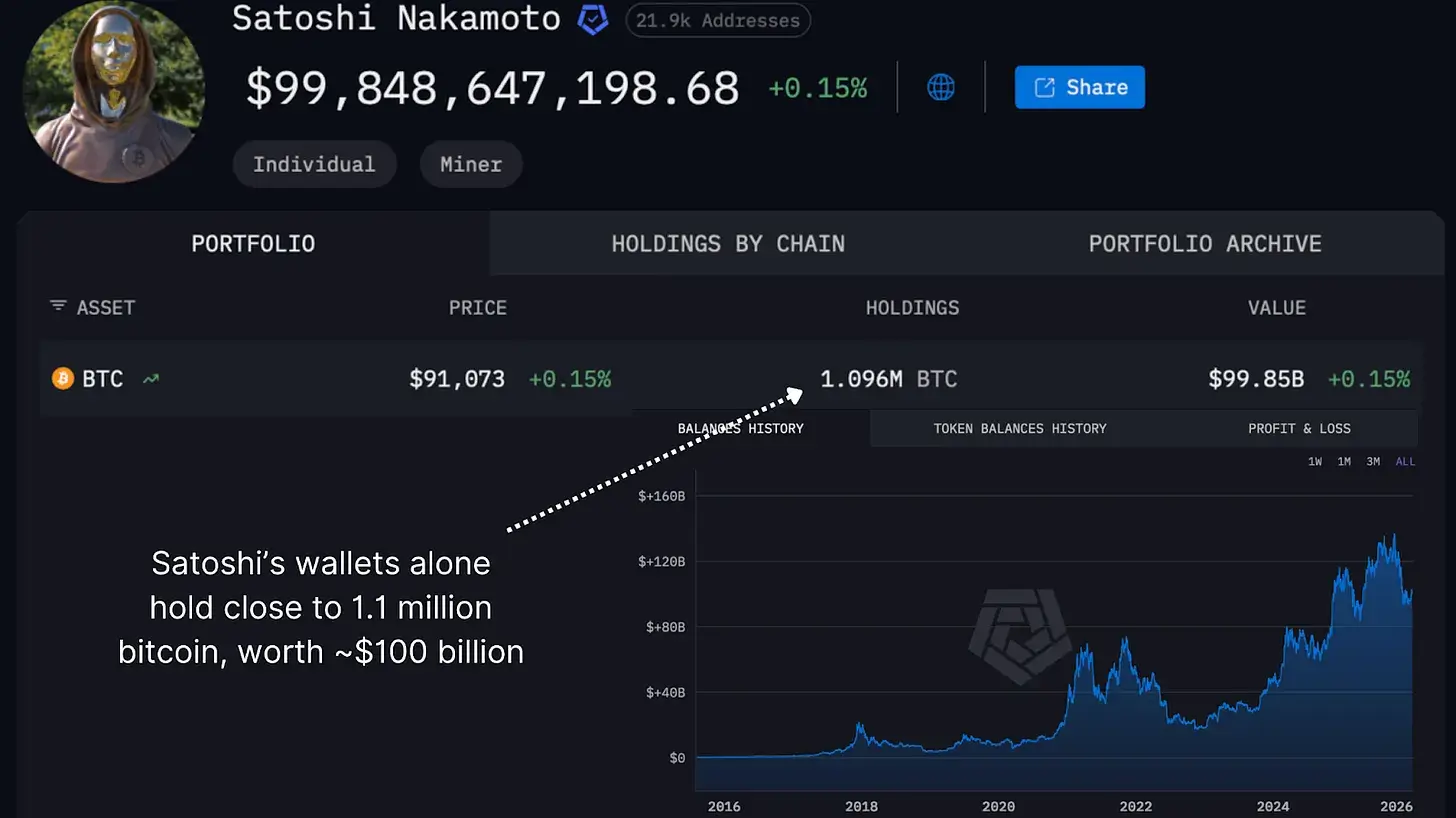
Figure 1: Satoshi Nakamoto's wallet holds nearly 1.1 million bitcoins.
Not all bitcoins face the same level of risk. Early Pay-to-Public-Key (P2PK) addresses, including Satoshi's, have their public keys directly visible on the ledger. For these bitcoins, a quantum computer is like a "master key" that can directly access the wallet. In contrast, later address types (like P2PKH) hide the public key behind a cryptographic hash, exposing it only when a transaction is initiated. This creates a brief window of vulnerability: between the moment you reveal the public key to send a transaction and when it is confirmed by miners, a sufficiently powerful quantum computer could theoretically intercept it.
Uncertain Timeline
The timeline for quantum computing is highly uncertain. It could arrive within a year, or it might never materialize. But uncertainty is the enemy because Bitcoin requires proactive migration, not reactive adaptation. If quantum computers emerge before Bitcoin has migrated to post-quantum cryptography (PQC), Bitcoin will be defeated. Trillions of dollars worth of public keys would be exposed, and attackers could begin stealing and dumping bitcoins onto the market, causing a catastrophic price collapse.
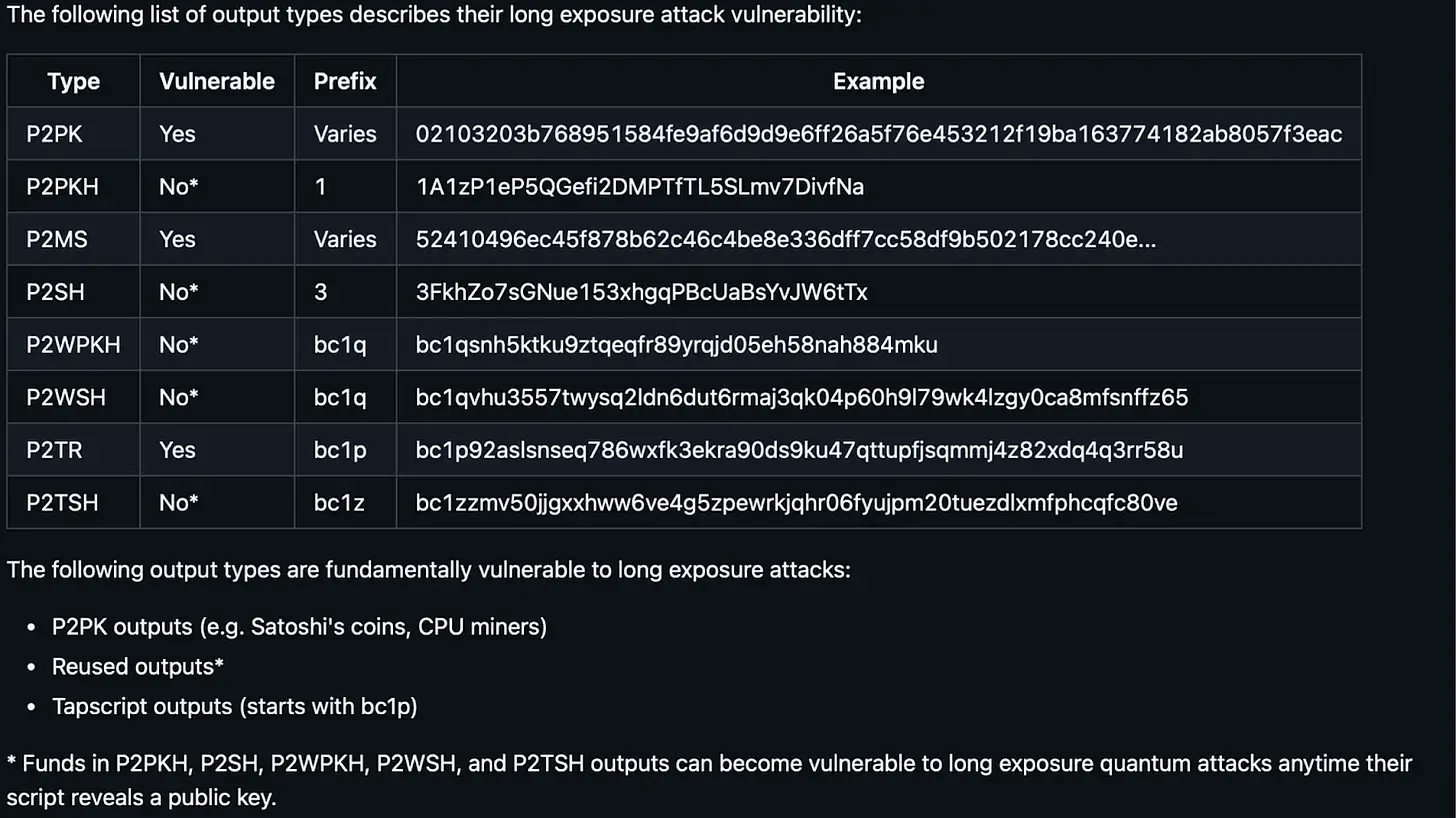
Figure 2: Comparison of long-term exposure attack vulnerabilities for different Bitcoin address types.
Under the most optimistic scenario, finalizing the code and reaching consensus for a PQC solution would take 6 to 12 months; depending on signature optimization, the migration process could require an additional 6 months to 2 years.
Coin Burning
The question is whether a deadline should be set to "burn" bitcoins that have not been migrated to quantum-resistant addresses by the cutoff date. If approximately 20-30% of the supply were simultaneously unlocked (compromised), Bitcoin would face a massive crisis of confidence, and its "hard money" thesis would collapse. A supply sell-off of this magnitude would create bear market conditions and could jeopardize Bitcoin's entire philosophy.
However, coin burning faces significant philosophical obstacles. It would essentially mean that Bitcoin property could become subject to confiscation. If the network decides it can redeem itself by burning coins, what would stop a government or controller from deciding which addresses (e.g., those of terrorists or dissidents) can be burned and censored? This would set a precedent that destroys the sovereign individual's ownership of assets.
Primary Target
Bitcoin is the world's largest "honeypot." It is the only financial network where you can directly steal value and have 24/7 liquidity to cash out. The US dollar cannot do this—stealing large sums leads to blocked transfers, and even if hacked, institutions refund customers. Bitcoin has no such luxury; it is built purely on trust in code.
Figure 4: The number of addresses holding over 10,000 BTC is significant.
If someone achieves quantum computing capability to break encryption, Bitcoin wallets will be the primary target because they are easier to liquidate and offer a first-mover advantage. If the money is already taken by the first cracker, the second will get nothing.
Conclusion
Although this existential-level vulnerability has long been recognized in cryptographic literature, the window for preventive action is narrowing, requiring immediate strategic attention from miners, exchanges, wallet providers, and individual stakeholders. The real test is not whether the threat exists, but whether the network can coordinate and methodically migrate to quantum-resistant signature algorithms before a quantum computer with sufficient computational power emerges.