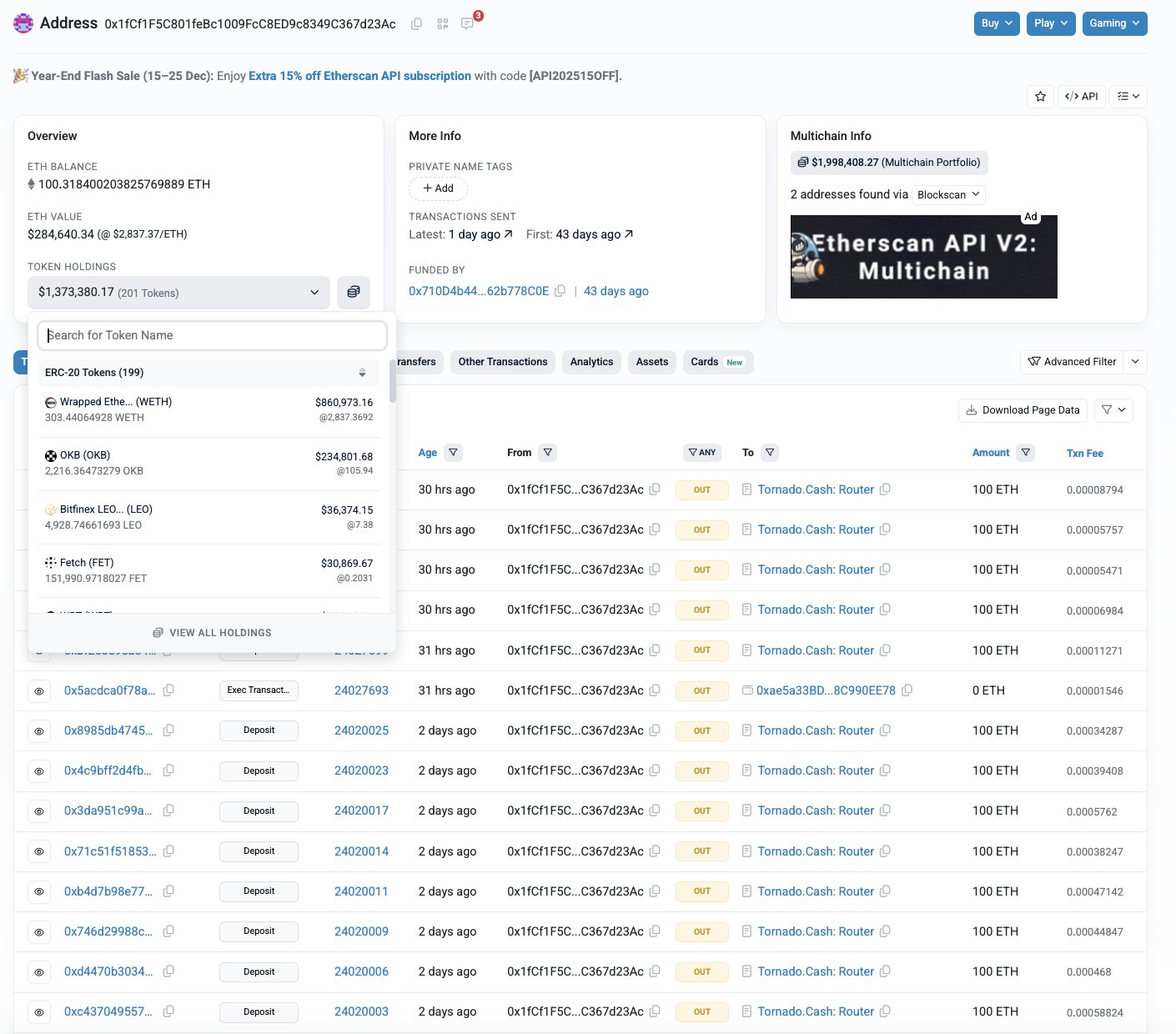
A crypto attacker apparently took over a whale’s multisig wallet minutes after it was created 44 days ago, and has been draining and laundering funds in stages since.
In a Thursday post on X, blockchain security firm PeckShield reported that a whale’s multisig wallet had been drained of roughly $27.3 million due to a private key compromise. PeckShield noted that the attacker has laundered about $12.6 million, or 4,100 Ether (ETH), through Tornado Cash and retained around $2 million in liquid assets, while also controlling a leveraged long position on Aave (AAVE).
However, new findings from Yehor Rudytsia, head of forensic at Hacken Extractor, indicate the total losses may exceed $40 million and that the incident likely began much earlier, with first signs of theft dating back as far as Nov. 4.
Rudytsia told Cointelegraph that the multisig wallet labeled as “compromised” may never have been meaningfully controlled by the victim. Onchain data shows the multisig was created by the victim’s account on Nov. 4 at 7:46 am UTC, but ownership was transferred to the attacker just six minutes later. “Very likely the theft actor created this multisig and transferred funds there, then promptly swapped the owner to be himself,” Rudytsia said.
Related: Spear phishing is North Korean hackers’ top tactic: How to stay safe
Attacker plays the long game
Once in control, the attacker appears to have acted patiently. They made Tornado Cash deposits in batches over several weeks, starting with 1,000 ETH on Nov. 4 and continuing through mid-December in smaller, staggered transactions. Around $25 million in assets also remains on the multisig still controlled by the attacker, according to Rudytsia.
He also raised concerns about the wallet structure. The multisig was configured as a “1-of-1,” meaning only a single signature was required to approve transactions, “which is not a multisig conceptually,” Rudytsia added.
Abdelfattah Ibrahim, a decentralized application (DApp) auditor at Hacken, said several attack vectors remain possible. These include malware or infostealers on the signer’s device, phishing attacks that trick users into approving malicious transactions, or poor operational security practices such as storing keys in plaintext or using the same machine for multiple signers.
“Preventing this would involve isolating signing devices as cold devices and verifying transactions beyond the UI,” Ibrahim said.
Related: Balancer community proposes plan to distribute funds recovered from hack
AI models capable of smart contract exploits
As Cointelegraph reported, a recent research by Anthropic and the Machine Learning Alignment & Theory Scholars (MATS) group found that today’s leading AI models are already capable of developing real, profitable smart contract exploits.
In controlled tests, Anthropic’s Claude Opus 4.5, Claude Sonnet 4.5 and OpenAI’s GPT-5 collectively generated exploits worth $4.6 million, showing that autonomous exploitation is technically feasible using commercially available models.
In further testing, Sonnet 4.5 and GPT-5 were deployed against nearly 2,850 recently launched smart contracts with no known vulnerabilities. The models uncovered two previously unknown zero-day flaws and produced exploits worth $3,694, slightly more than the $3,476 API cost required to generate them.
Magazine: 2026 is the year of pragmatic privacy in crypto — Canton, Zcash and more