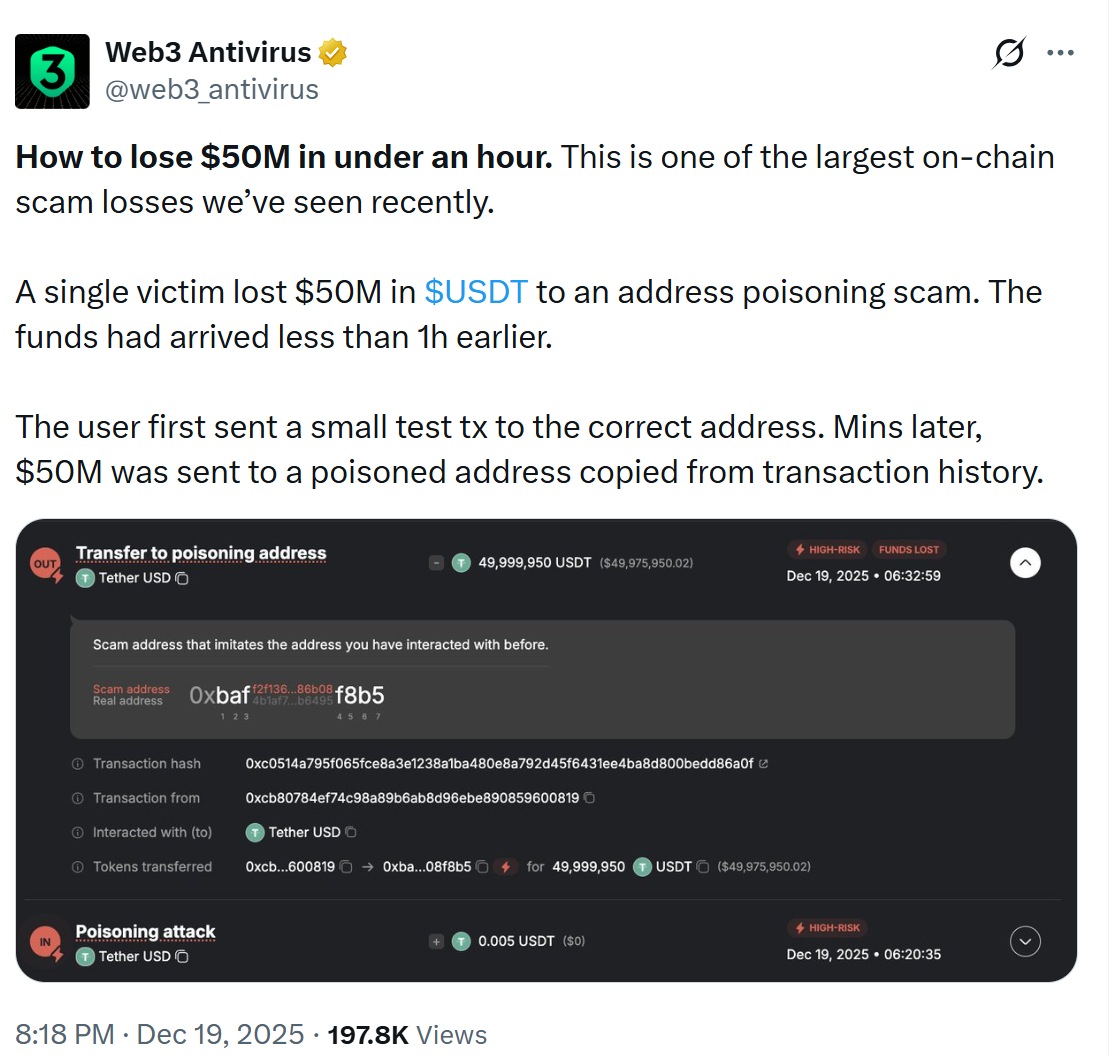
A single transaction error led to one of the largest onchain losses seen this year, after a user mistakenly sent nearly $50 million in USDt to a scam address in a classic address poisoning attack.
According to onchain investigator Web3 Antivirus, the victim lost 49,999,950 USDt (USDT) after copying a malicious wallet address from their transaction history.
Address poisoning scams rely on look-alike wallet addresses being inserted into a victim’s transaction history via small transfers. When victims later copy an address from their transaction history, they may unknowingly select the scammer’s lookalike address instead of the intended recipient.
Onchain data shows the victim initially sent a small test transaction to the correct address. Minutes later, however, the full $50 million transfer was sent to the poisoned address.
Related: Attacker takes over multisig minutes after creation, drains up to $40M slowly
Subtle address similarity enough to fool experienced users
Security researcher Cos, founder of SlowMist, noted the similarity between the addresses was subtle but enough to deceive even experienced users. “You can see the first 3 characters and last 4 characters are the same,” he wrote.
The victim’s wallet had been active for roughly two years and was primarily used for USDt transfers, according to onchain analysis. Shortly before the loss, the funds were withdrawn from Binance, suggesting the wallet was being actively managed at the time of the incident.
“This is the brutal reality of address poisoning, an attack that doesn’t rely on breaking systems, but on exploiting human habits,” another onchain analyst wrote.
The attacker has since swapped the stolen USDt for Ether (ETH), splitting it into multiple wallets, and partially moved it into Tornado Cash.
Related: Binance denies reports of delayed action over funds linked to Upbit hack
Crypto hacks hit $3.4 billion in 2025
As Cointelegraph reported, crypto-related hacks resulted in $3.4 billion in losses in 2025, marking the highest annual total since 2022. The surge was largely driven by a handful of massive breaches targeting major crypto entities rather than a broad rise in average attack size.
Just three incidents accounted for 69% of total losses this year, led by the $1.4 billion hack of crypto exchange Bybit, which alone made up nearly half of all stolen funds.
Magazine: 2026 is the year of pragmatic privacy in crypto — Canton, Zcash and more