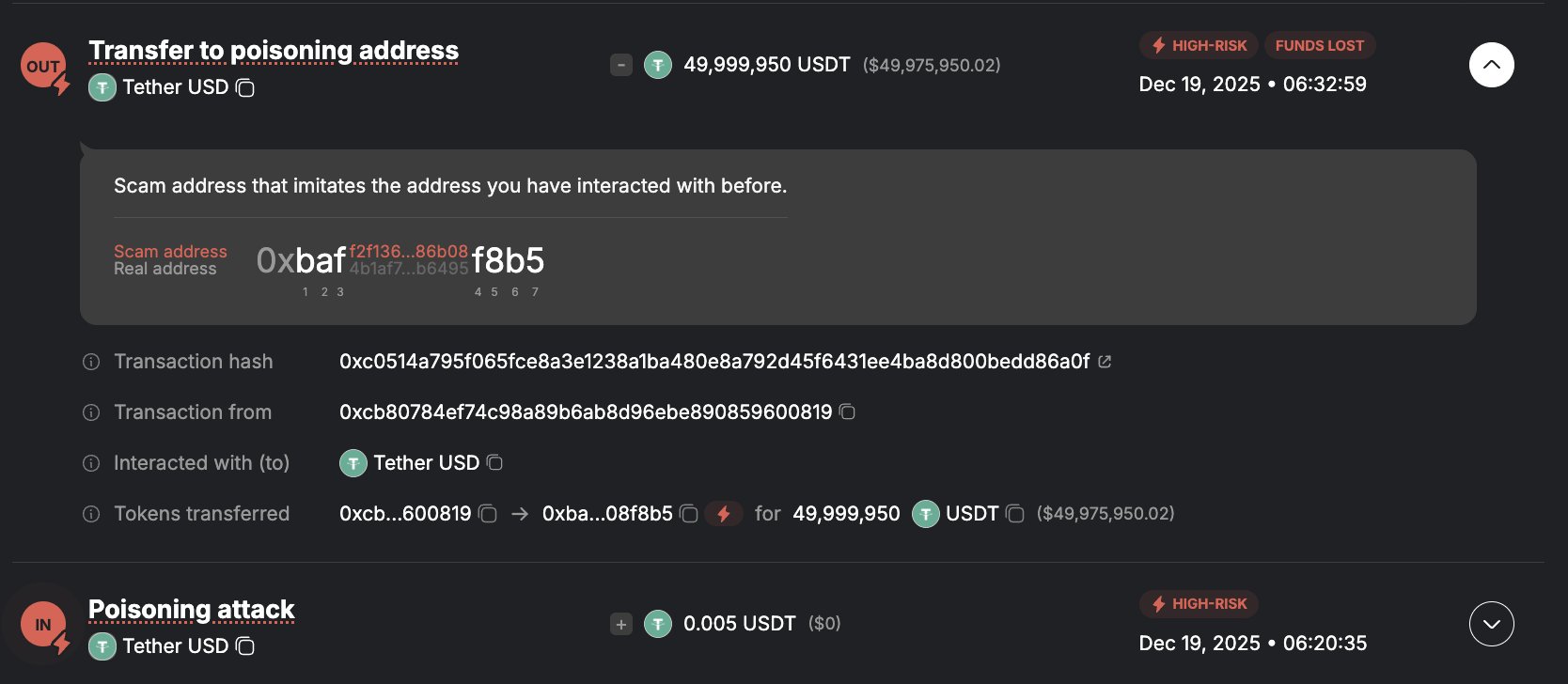
An unsuspecting crypto user has recently lost $50 million USDT in an address poisoning scam. The incident represents one of the largest on-chain losses in 2025, drawing reactions from crypto security experts as new developments on the matter roll in.
Copy-Paste Mistake Costs User 50M USDT
Address poisoning is a scam in which an attacker sends small transactions from a wallet address that closely resembles a victim’s legitimate address, hoping the victim will later copy the wrong address from their transaction history and unknowingly send funds to the attacker.
Blockchain security page, Web3 Antivirus reports that a crypto user recently fell victim to this scam, sending 49,999,950 USDT to a poisoned address copied from transaction history. Considering the large transaction, the user had tried taking caution by sending a small test transaction to the correct address. However, the nature of address poisoning requires close monitoring, where attackers are able to immediately send dust transactions from wallets resembling the intended address.
Cos, founder of fellow security platform Slowmist, provided valuable insights on this operation, noting the similarity between both addresses, which shared the same first 3 characters and last 4 characters. The victim unknowingly picked the poisoned address from the transaction history to complete the $50 million, thus marking one of the biggest on-chain individual losses of 2025.
More data from Web3 Antivirus reveals that the victim wallet has been active on-chain for approximately two years and is primarily used for USDT transfers. The stolen $50 million was also initially withdrawn from Binance before the scam occurred. Notably, the stolen USDT has since been converted to ETH by the attackers and shared among multiple wallets, who have also funneled some of the loot through Tornado Cash.
Address Poisoning Victim Offers Bounty With 48-Hour Ultimatum
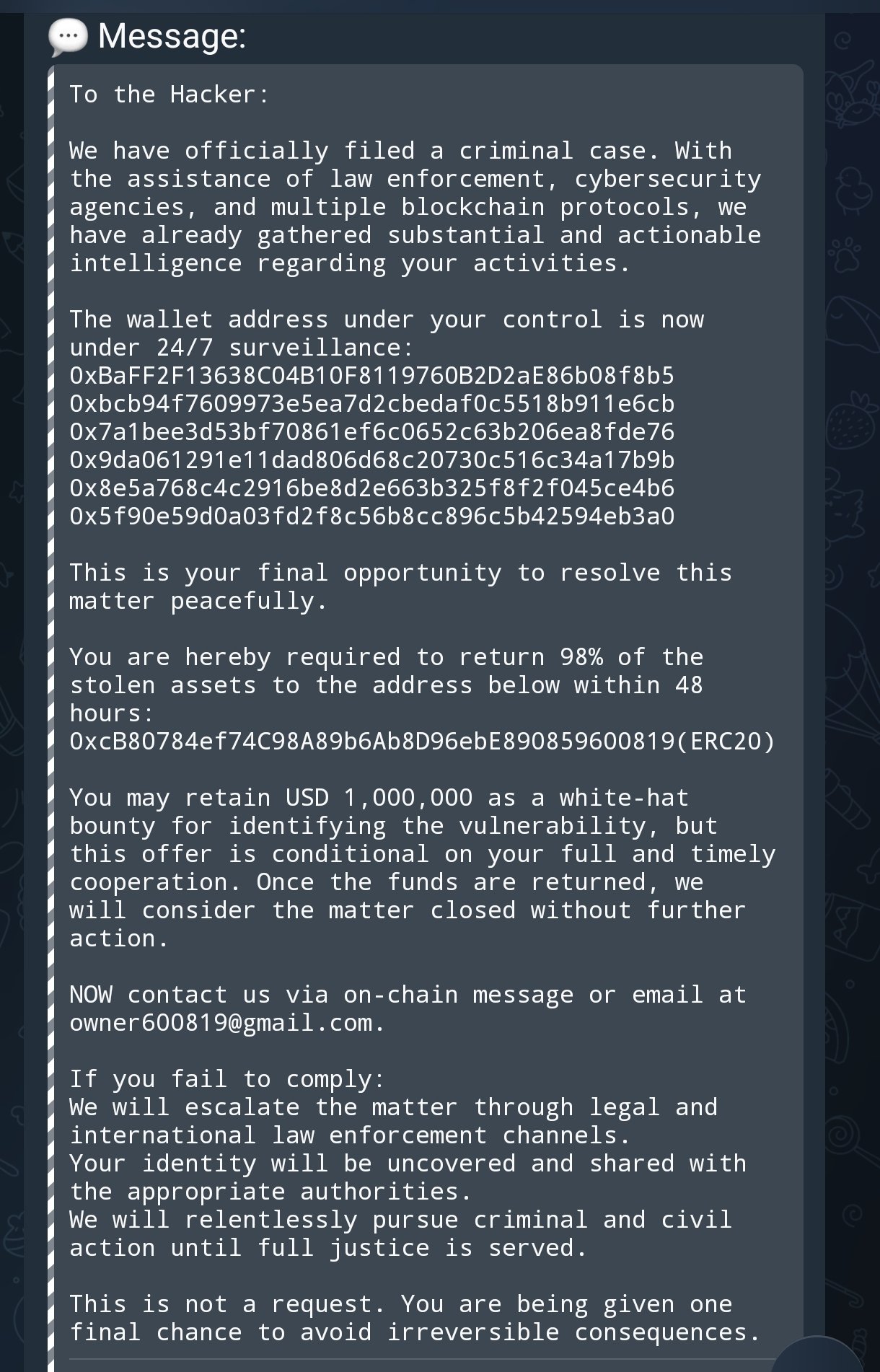
In other news, blockchain investigator Specter Analyst reports that the victim has attempted to establish communication with the attackers via an on-chain message.
According to an X post on December 20, the victim claims to have filed a criminal complaint case while also enlisting the relevant law enforcement, cybersecurity, and blockchain protocols to provide needed intelligence on the scammer’s activities. Furthermore, all six addresses associated with the heist are now under constant surveillance. However, the aggrieved party is offering the perpetrators of the address poisoning a peaceful resolution, which involves the willing return of 98% of the loot to a specified address within 48 hours.
Notably, the victim will allow the bad actors to keep $1 million as a bug bounty for spotting such a vulnerability in their operations. However, they warn that failure to accept the amicable offer within the stipulated time will result in legal escalation of the matter to international law enforcement authorities. They further warn that the attackers’ identities will be revealed and shared with the relevant agencies to aid their arrest and persecution. At press time, total crypto losses in 2025 have surpassed $3.4 billion, underscoring the need for continually strengthened security measures within the thriving ecosystem.